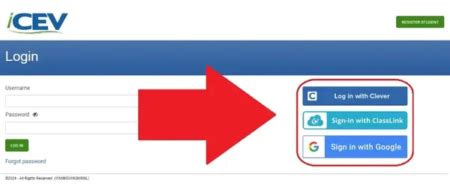
In an era where digital security is paramount, managing access to sensitive information and platforms requires more than just conventional passwords. As cyber threats evolve in complexity and frequency, comprehensive and multi-layered authentication methods have become essential. Among emerging solutions, Icev.login offers a promising paradigm shift by providing a seamless, secure, and user-friendly access experience. This article explores the intricacies of Icev.login, dissecting its architecture, implementation strategy, and practical benefits, all grounded in the latest industry standards and expert insights.
Understanding the Foundation of Secure Access Systems

Before delving into Icev.login, it’s crucial to grasp the foundational principles of secure access management. Traditional authentication mechanisms predominantly relied on static credentials—usernames and passwords—that, while convenient, present vulnerabilities such as phishing, brute-force attacks, and credential reuse. Consequently, modern security frameworks emphasize multifactor authentication (MFA), zero-trust models, and continuous verification processes.
In the context of organizational cybersecurity, a layered approach—often designated as defense-in-depth—ensures that a single point of failure cannot compromise entire systems. This philosophy underpins Icev.login, designed to integrate seamlessly with existing security architectures while enhancing robustness through novel authentication techniques.
Introducing Icev.login: Features and Architectural Overview
Icev.login distinguishes itself through an architecture crafted for adaptability, security, and ease of integration. At its core, it leverages cutting-edge cryptographic protocols, adaptive risk assessment algorithms, and biometrics to authenticate users. The system’s modular design facilitates deployment across diverse platforms—from enterprise dashboards to mobile applications—while maintaining consistency in security standards.
Core Components of Icev.login
Salient features include:
- Multifactor Authentication (MFA): Combining something you know (password), something you have (device token), and something you are (biometric verification).
- Risk-based Authentication: Dynamic assessment of user behavior, device reputation, geolocation, and network context to determine authentication strength.
- End-to-End Encryption: Ensuring data confidentiality during transmission and storage through AES-256 and RSA encryption standards.
- Universal Compatibility: Support for OAuth 2.0, OpenID Connect, and SAML protocols for seamless integration into existing identity frameworks.
Step-by-Step Implementation of Icev.login
Successfully deploying Icev.login involves a systematic approach that aligns with best practices in identity and access management (IAM). The following stages delineate this process with technical precision and actionable guidance:
1. Infrastructure Assessment and Preparation
Begin by evaluating existing systems, network architecture, and security policies. This assessment ensures compatibility and identifies potential integration points. For instance, verifying support for OAuth or SAML is critical for smooth adoption. Infrastructure provisioning includes setting up secure servers, establishing encrypted communication channels, and defining access control policies.
2. Integration with Identity Providers
Next, configuration involves connecting Icev.login to Identity Providers (IdPs) like Active Directory, LDAP, or cloud-based solutions such as Azure AD. Proper mapping of user attributes and establishing trust relationships through secure certificates set the foundation for federated authentication.
3. Configuring Authentication Factors
Depending on organizational security requirements, administrators can configure multifactor mechanisms. For example, enabling biometric verification on mobile devices coupled with hardware tokens enhances security posture. Fine-tuning risk-based heuristics involves defining threshold parameters for adaptive authentication responses.
4. User Enrollment and Education
Implement a robust onboarding process that guides users through enrollment, including device registration, biometric data capture, and familiarity with MFA prompts. Clear communication reduces resistance and enhances compliance.
5. Testing and Validation
Rigorous testing in staging environments helps to identify potential gaps or vulnerabilities. Simulate attack scenarios such as credential stuffing or man-in-the-middle attacks to validate resilience. Ensuring logging mechanisms are operational supports auditability and incident response.
6. Deployment and Monitoring
Gradual rollout accompanied by real-time monitoring allows for quick adjustments. Use analytic dashboards to observe sign-in success rates, failed attempts, and anomaly detection alerts. Continuous monitoring underpins the proactive threat mitigation process.
| Implementation Step | Critical Consideration |
|---|---|
| Infrastructure Assessment | Compatibility and capacity planning to handle user load and security demands |
| IdP Integration | Secure trust establishment and attribute synchronization |
| Authentication Factors Configuration | Balancing usability and security, contextual risk assessment |
| User Enrollment | Clear instructions and support mechanisms for users |
| Testing | Simulate diverse attack vectors for resilience validation |
| Deployment | Phased approach with ongoing performance metrics |
Advantages of Using Icev.login Over Traditional Access Methods
Transitioning from conventional passwords to advanced access mechanisms offers tangible benefits. Not surprisingly, organizations reporting implementation of Icev.login or similar solutions record notable improvements in security metrics, user satisfaction, and operational efficiency.
Enhanced Security Posture
By integrating multifactor authentication, risk-based adaptive measures, and biometric verification, Icev.login significantly reduces the probability of unauthorized access. According to recent industry reports, MFA can prevent up to 99.9% of account compromise risks, particularly when combined with behavioral analytics.
Streamlined User Experience
Innovative features such as biometric login and single sign-on (SSO) simplify user workflows, reducing login times and diminishing password fatigue. The frictionless aspect encourages adherence to security protocols without compromising convenience.
Compatibility and Scalability
Supporting multiple protocols and platform integrations, Icev.login caters to diverse organizational needs—from small startups to large enterprises. Its scalable architecture ensures that security enhancements do not impair performance or user accessibility.
Auditability and Compliance
Comprehensive logging and reporting foster transparency and facilitate compliance with standards like GDPR, HIPAA, and PCI DSS. Automated audit trails expedite investigations and support regulatory mandates.
Potential Limitations and Challenges in Deployment

Despite its benefits, deploying Icev.login is not without hurdles. Technical complexity, user resistance, and integration overhead can impede swift adoption. For instance, biometric registration accuracy varies due to environmental factors, and device compatibility issues may arise, necessitating careful planning.
Moreover, organizations must constantly update security policies in response to emerging threats. The management of biometric data also raises privacy considerations that require transparent policies compliant with data protection regulations.
Addressing User Resistance and Privacy Concerns
Employing comprehensive training programs and transparent communication alleviates user apprehensions. Clear policy articulation regarding biometric data handling, storage, and usage engenders trust and compliance.
Technical Complexity and Maintenance
Integrating Icev.login within legacy systems might demand custom development efforts. Regular updates, patch management, and auditing are necessary to sustain system integrity. Nonetheless, these initiatives contribute to long-term security resilience.
Key Points
- Security Enhancement: Multifactor and adaptive authentication significantly reduce breach risks.
- User Experience: Biometric login and single sign-on streamline workflows.
- Integration Flexibility: Compatible with existing identity providers and protocols.
- Implementation Strategy: Structured, phased deployment maximizes success and minimizes disruption.
- Future Trends: Scalability and behavioral analytics position Icev.login as a future-ready solution.
How does Icev.login improve overall security compared to traditional password systems?
+Icev.login incorporates multifactor authentication, risk-based adaptive elements, and biometric verification, drastically lowering the chances of unauthorized access. While passwords are susceptible to theft and reuse, the layered approach provides multiple hurdles, making breaches exceedingly difficult—up to 99.9% prevention efficacy according to industry studies.
What are the main challenges when deploying Icev.login in an existing enterprise environment?
+Challenges include technical integration with legacy systems, user resistance to new authentication processes, privacy concerns related to biometric data, and maintaining system updates. Addressing these requires careful planning, user education, and compliance with data privacy regulations, but the benefits in security resilience are substantial.
Can Icev.login adapt to evolving cybersecurity threats?
+Yes, its modular and adaptive architecture supports evolving authentication methods, including behavioral biometrics and decentralized identity solutions. Continuous updates and risk management protocols ensure that Icev.login remains resilient against emerging threats and vulnerabilities.