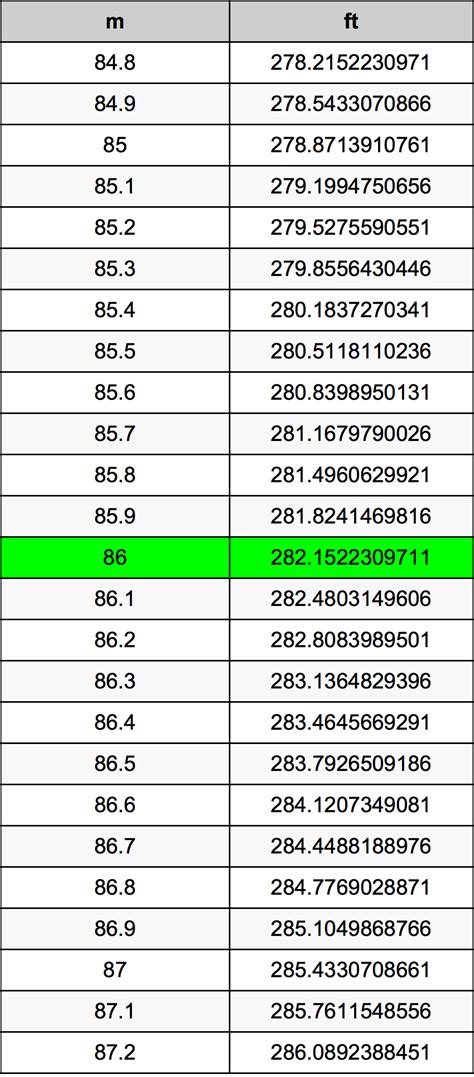
The world of cybersecurity is constantly evolving, with new threats and vulnerabilities emerging every day. As a result, the need for innovative login solutions has never been more pressing. Traditional password-based authentication methods are no longer sufficient, and businesses are looking for more secure and user-friendly alternatives. In this article, we will explore five new login innovations that are changing the way we think about authentication and security.
Key Points
- Biometric authentication is becoming increasingly popular due to its high level of security and convenience
- Behavioral biometrics can provide an additional layer of security by analyzing user behavior and patterns
- Quantum-resistant cryptography is essential for protecting against future quantum computer attacks
- Zero-knowledge proofs can enable secure authentication without revealing sensitive information
- Decentralized identity management can provide users with more control over their personal data and identity
Biometric Authentication: The Future of Secure Logins
Biometric authentication uses unique physical or behavioral characteristics, such as fingerprints, facial recognition, or voice recognition, to verify a user’s identity. This method is becoming increasingly popular due to its high level of security and convenience. With biometric authentication, users no longer need to remember complex passwords or carry around physical tokens. Instead, they can simply use their unique biological characteristics to access their accounts and devices.
Types of Biometric Authentication
There are several types of biometric authentication, including:
- Fingerprint recognition: uses unique fingerprint patterns to verify identity
- Facial recognition: uses facial features and patterns to verify identity
- Voice recognition: uses unique voice patterns and characteristics to verify identity
- Iris scanning: uses the unique patterns in the iris to verify identity
Behavioral Biometrics: Analyzing User Behavior for Enhanced Security
Behavioral biometrics takes biometric authentication to the next level by analyzing user behavior and patterns. This method can provide an additional layer of security by detecting and preventing suspicious activity. Behavioral biometrics can analyze a range of factors, including:
- Typing patterns and rhythms
- Mouse movements and gestures
- Device usage and activity patterns
- Location and time of access
Benefits of Behavioral Biometrics
The benefits of behavioral biometrics include:
- Improved security: behavioral biometrics can detect and prevent suspicious activity in real-time
- Enhanced user experience: behavioral biometrics can provide a seamless and frictionless authentication experience
- Increased accuracy: behavioral biometrics can provide more accurate results than traditional biometric authentication methods
Quantum-Resistant Cryptography: Protecting Against Future Attacks
Quantum computers have the potential to break many of the encryption algorithms currently in use, compromising the security of online transactions and data. Quantum-resistant cryptography is essential for protecting against these future attacks. This method uses algorithms that are resistant to quantum computer attacks, ensuring that data remains secure and protected.
Types of Quantum-Resistant Cryptography
There are several types of quantum-resistant cryptography, including:
- Lattice-based cryptography: uses complex mathematical problems to secure data
- Code-based cryptography: uses error-correcting codes to secure data
- Hash-based cryptography: uses cryptographic hash functions to secure data
Zero-Knowledge Proofs: Secure Authentication Without Revealing Sensitive Information
Zero-knowledge proofs enable secure authentication without revealing sensitive information. This method allows users to prove their identity without sharing their personal data or credentials. Zero-knowledge proofs use complex mathematical algorithms to verify identity, ensuring that sensitive information remains secure and protected.
Benefits of Zero-Knowledge Proofs
The benefits of zero-knowledge proofs include:
- Improved security: zero-knowledge proofs can provide secure authentication without revealing sensitive information
- Enhanced user experience: zero-knowledge proofs can provide a seamless and frictionless authentication experience
- Increased privacy: zero-knowledge proofs can protect user data and prevent identity theft
Decentralized Identity Management: Giving Users Control Over Their Personal Data
Decentralized identity management gives users more control over their personal data and identity. This method uses blockchain technology to create a secure and decentralized identity management system. Users can store their personal data and credentials on a secure blockchain, ensuring that they have full control over their identity and data.
Benefits of Decentralized Identity Management
The benefits of decentralized identity management include:
- Improved security: decentralized identity management can provide secure storage and management of personal data
- Enhanced user experience: decentralized identity management can provide a seamless and frictionless authentication experience
- Increased control: decentralized identity management gives users full control over their personal data and identity
| Login Innovation | Description |
|---|---|
| Biometric Authentication | Uses unique physical or behavioral characteristics to verify identity |
| Behavioral Biometrics | Analyzes user behavior and patterns to detect and prevent suspicious activity |
| Quantum-Resistant Cryptography | Uses algorithms that are resistant to quantum computer attacks to secure data |
| Zero-Knowledge Proofs | Enables secure authentication without revealing sensitive information |
| Decentralized Identity Management | Gives users more control over their personal data and identity using blockchain technology |

What is biometric authentication, and how does it work?
+Biometric authentication uses unique physical or behavioral characteristics, such as fingerprints, facial recognition, or voice recognition, to verify a user's identity. This method is becoming increasingly popular due to its high level of security and convenience.
What are the benefits of behavioral biometrics, and how does it enhance security?
+Behavioral biometrics can provide an additional layer of security by detecting and preventing suspicious activity. This method analyzes user behavior and patterns, such as typing patterns and mouse movements, to verify identity and prevent unauthorized access.
What is quantum-resistant cryptography, and why is it essential for protecting against future attacks?
+Quantum-resistant cryptography uses algorithms that are resistant to quantum computer attacks to secure data. This method is essential for protecting against future attacks, as quantum computers have the potential to break many of the encryption algorithms currently in use.
In conclusion, these five new login innovations have the potential to revolutionize the way we think about authentication and security. By providing users with a seamless and secure experience, businesses can protect their data and prevent unauthorized access. As we move forward in the digital age, it’s essential to prioritize security and convenience, and these innovations are a significant step in the right direction.